- TechJourney Newsletter
- Posts
- Foundations
Foundations
The secondedition of my Newsletter
Hi Folks,
and welcome to the second edition of my newsletter.
During the last week, I have been working on configuring TLS in one of the applications on my job. It is an HTTP server that manages other applications and supports HTTP but we had the decision to make it more secure. So we need to move it to HTTPS. And I thought it would be a good idea to share it here in the newsletter :)
HTTPS works over TLS and you are probably aware of TLS and have already used it many times - anytime you use a browser you may see a small lock icon near the address line.
That means your connection is secured with TLS.
TLS is a secure layer above TCP protocol. It uses asymmetric and symmetric cryptography for securing connections between client and server.
Symmetric cryptography is effective in the encryption and decryption of traffic because of its key length. But it has the disadvantage of exchanging the secret key. Both parties should have the same key to encrypt and decrypt the traffic.
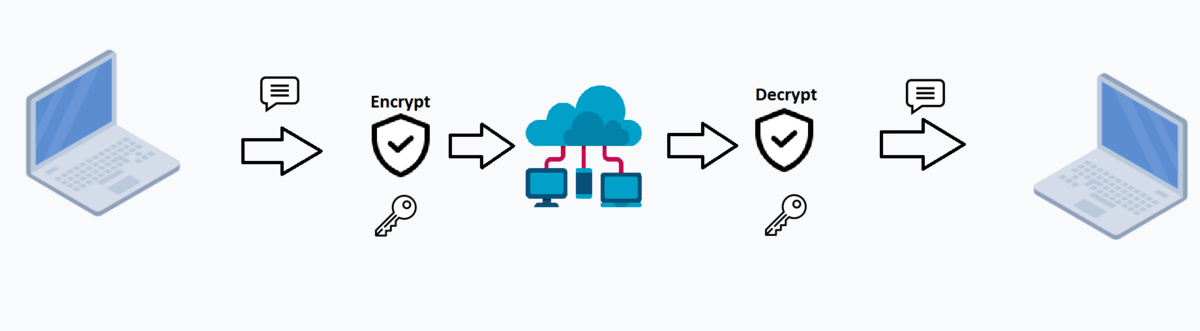
Fortunately, this problem was solved with asymmetric cryptography.
Being not so effective in encryption/decryption, asymmetric crypto has it is the main advantage for web apps - it can safely exchange secrets because of public and private keys. You can use your private key to decrypt the message that is addressed to you and the public to encrypt.
Because of the advantages and disadvantages of symmetric and asymmetric crypto, TLS uses it in a combined way and that makes it effective. So what happens when you connect to your favorite website from your browser:
your browser is the client and going to connect to the server
It opens a TCP session, here is going, TCP-handshake staff
right after we have the TLS handshake. Briefly speaking, at this stage client, asks the server to provide its TLS certificate, in other words, his public key (yeah, asymmetric crypto in da house)
also during this stage clients and servers decide which algorithm used to encrypt the traffic and generate a session key
and voila - we have made a TLS connection
The public key ensures that the host provided the public key is authentic because the public key is issued by a trusted Certificate Authority. Your browser and OS have preinstalled CAs that are trusted, hence if the public key is provided by one of these CAs it will be valid otherwise you might see Note that the connection is insecure
So by generating a TLS certificate for our server we solved the problem of securing traffic.
Self-learning topics
I continue reading "But How Do It Know? - The Basic Principles of Computers for Everyone", which is not a big book, but I don't spend much time on it.
It is a great refresher about the nutshells of computers and why programmers need to know discrete math :)
You are probably aware the smallest unit that a computer operates is a bit. And eight bits equal to byte ... binary and hex staff and blah-blah-blah. But let's stick to the bit.
A bit can store a 0 or 1 and that is all. In a computer, everything is nothing but 0's and 1's bits. And here I have a good statement from the book:
A computer bit is still, and will always be, nothing more than a place where there is or is not electricity, but when we, as a society of human beings, use a bit for a certain purpose, we give meaning to the bit.
To store electricity that will be meaningful for us people created tiny things called logic gates. And computers totally consist of them. There are the main ones: NAND, AND, OR, and XOR, but the NAND gate is the universal one.
All basic gates are created using the NAND gate. They are not just called logical - they correspond to logical operators that you might see in logic class or discrete math - you can build Truth Table for it.
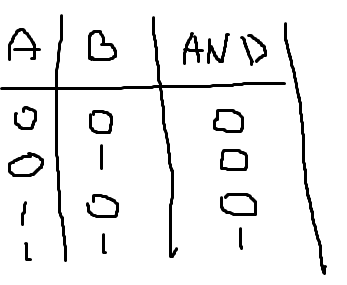
And those tiny little things are the base of everything of the computer. So I like this book, it is easy to read and hard content is explained in an easy way anyone can understand.
Also, I spend some time searching for learning resources for my domain specialty -cybersecurity. Although I am not usually work in this domain I need to practice and learn new stuff. Hence from time to time, I am searching for new courses or white papers/bug bounty reports to be in good shape.
For now, in the nearest future I plan to dive into the following platforms:
Pentesterlab
TryHackMe
HackTheBox
It is mostly about Web-Application Pentesting, but there are also read team-related labs.
Thank you again, and if you want to discuss any ideas from my writings you can reach me via email, feel free to reply.
Best Regards,
Alex