- TechJourney Newsletter
- Posts
- What is JWT
What is JWT
Part 1 Briefly about JWT
From this publication, I am starting a series of learning posts. I am going to refresh my tech knowledge on different topics and share something here. Today I will talk about the JWT token. This post will be split into 3 parts.
This post relates more to security and touches on authentication and authorization concepts.
You face these concepts on daily basis:
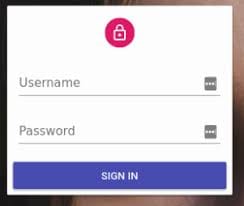
You probably know what this form is about. You fill in your login and password in order to access a site. And the process of verifying your credentials by the server is named authentication. Briefly, you answer “are you the one who you say you are ?”
If you are how you claim you are - password and login are correct - server accepts it - you logged in successfully
Sometimes you need to access specific web service resources - verifying your permissions to access any resources is done by checking corresponding security rules and policies, i.e if you are not an admin you can not access the admin board.
In order server to know who is accessing any endpoint/route, after the successful login of the client, it sends a specific object - a cookie with the client's session id, and in the subsequent client's request, this cookie is sent as a part of the request. Servers authorize the user, having verified the cookie:
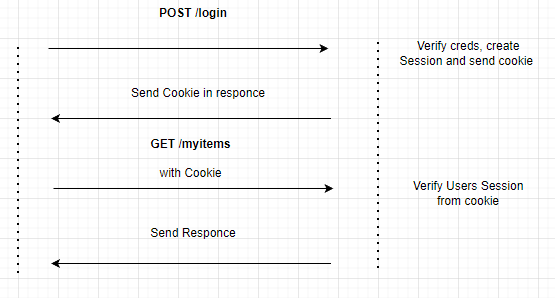
That solution is not suitable for distributed and scaled systems where clients can communicate with different backend servers that in that case need to store or share the somehow with each other the session cookie.
And JWT helps here, from RFC 7519:
JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties. The claims in a JWT are encoded as a JSON object that is used as the payload of a JSON Web Signature (JWS) structure or as the plaintext of a JSON Web Encryption (JWE) structure, enabling the claims to be digitally signed or integrity protected with a Message Authentication Code (MAC) and/or encrypted.
In general JWT token is a string:
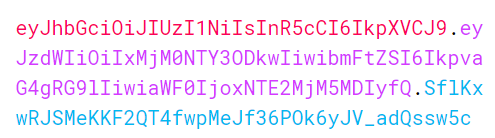
That consists of 3 parts (from the picture above):
Header → eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
Body → eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ
Signature → SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5c
Each part is encoded in base64 and after decoding we can see:
Header → { "alg": "HS256", "typ": "JWT" }
Usually contains algorithm used for signature and type of token
Body → { "sub": "1234567890", "name": "John Doe", "iat": 1516239022 }
Contains meaningful data need for user identity, authorization, expiration time, etc
Signature -> the digital signature, that is generated in the following way
HMACSHA256( base64UrlEncode(header) + "." + base64UrlEncode(payload), secret )
The data needed to be verified by the server can be taken from the client and stored within JWT which offloads the server from the need to store the session and constantly communicate with DB. And data integrity is protected by the signature.
The signature is generated on the server side using secret, which obviously should not be exposed anywhere.
The signature ensures that the Data Integrity of the JWT is not violated.
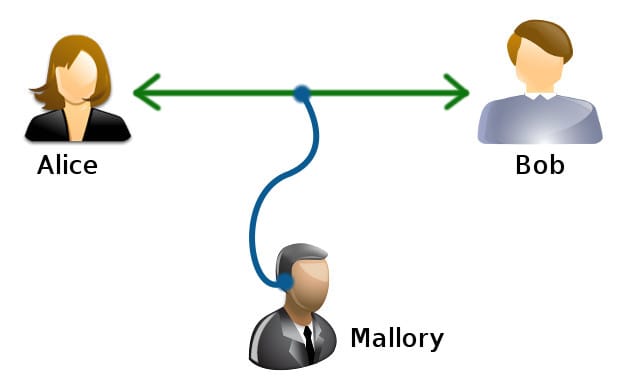
Data integrity means that data is not corrupted or not modified by parties that are not authorized to do this, let’s see the example below:
There are Alice and Bob sending data to each other and there is Mallory that is eavesdropping their communication
At some period of time Alice send some sensitive message to Bob,
{Bob you should go to the X city right now}
but Mallory intercepted it, then modified the message and resend it to Bob
{Bob you should go to the Y city right now}
As result, Bob receives the corrupted message.
In this example, Data integrity was violated
if Alice added a signature to the message
{Bob you should go to the X city right now}.signature
then Mallory could not modify it without being detected, except he has a key that was used to generate the signature,
having the mentioned characteristics JWT is a good solution for distributed and scalable web services and can be used for Authentication and Authorization in your web service preventing unwanted access to protected resources of your API.
JWT can be sent in HTTP headers, URLs, or cookies.
Example:
curl https://exampledomain.io/v1/api/getsomething -H "Accept: application/json" -H "Authorization: Bearer {token}"
That is all for now, in the next part I am going to set up a simple HTTP server in golang and configure JWT authentication and authorization there.
Thank you for your time,
BR,Alex